Cyber security: Peace of mind for your company
As the digitalisation of processes and the complexity of the IT landscape grow, so too does the risk of cyberattacks. The Federal Office for Information Security (BSI) has identified cyberattacks using ransomware as the main IT security threat to companies and administrative bodies in Germany.
The statistics on the losses caused by data theft, industrial espionage and sabotage in Germany in 2023 alone (source: Statista) paint an alarming picture: losses totalled more than EUR 200 billion, with the greatest losses seen in the fields of reputational damage (EUR 35 billion), malfunctioning/damage to IT systems and operational downtimes (EUR 35 billion), and costs for legal disputes (EUR 30 billion).
A global survey conducted in 2023 found that around 58 percent of the companies surveyed in Germany had fallen victim to a cyberattack at least once. On average, around 53 percent of the companies surveyed from the various countries stated that they had experienced at least one cyberattack in the past twelve months.
Luther’s multidisciplinary Cyber Security and Data Protection practice helps clients manage cyber security risks and attacks. With the support of our team of more than 40 experts, our clients can rise to any challenge relating to cyber security, incident response, data protection and, where applicable, embedded AI. As experienced “cause (or cyber) coaches,” we offer practical, technical and operational advice during and after ransomware attacks and other cyberattacks. With our first-hand experience, we operate on the interface between technology, cyber security and data protection for our clients.
Our advisory services can be divided into four areas:
The prevention of cyber incidents (cyber audits to develop an understanding and create awareness, documentation, training), the (crisis) response to cyber incidents (launching an emergency plan, securing relevant assets, involving the emergency team, B2B communication, communication with authorities, etc.), the pursuit of claims and litigation to enforce claims (ensuring compliance with personnel and technical requirements, insurance, etc.) and a regular future security audit.
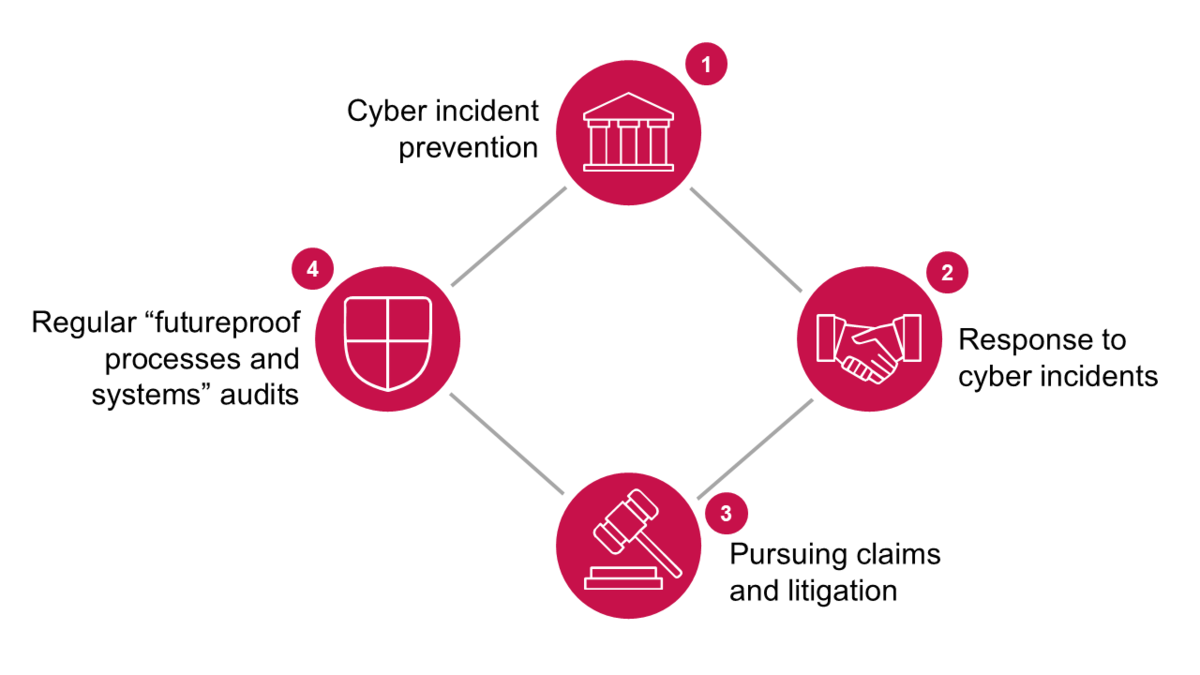
Areas of advice
The legal requirements regarding IT security are constantly changing and differ from industry to industry. These requirements not only stem from laws but also from industry-specific safety standards, technical standards, contractual relationships and liability risks. Our IT security law experts determine which legal requirements apply to your company and what action you need to take with regard to these requirements. Thanks to our industry knowledge and our understanding of complex corporate structures, we know that a secure, yet pragmatic implementation of legal requirements is the basis for company growth in times of digital transformation.
Our cyber security audit comprises a wide range of advisory services that review the processes and systems currently in place at your company to secure company data from a legal perspective. Implementing technical, operational and organisational measures to ensure IT security is essential if you wish to protect your company from damage caused by cyberattacks. We support you from the initial gap analysis through to the implementation of guidelines, instructions, training and other legal, operational and organisational measures. Our network of experts includes technical consultants who can provide support when it comes to identifying and implementing technical measures.
The protection of personal data is closely linked to the implementation of legal IT security requirements. After all, cyber incidents often involve personal data, which in turn gives rise to specific obligations when dealing with such incidents. Conversely, cyber security is always a means of protecting personal data. As a result, there are synergies to leverage between cyber security and data protection, particularly when implementing technical and organisational measures.
Cyber incidents may result in heavy fines or other regulatory measures imposed by the (data protection) supervisory authorities. Our specialised team can also advise you on communicating with supervisory authorities and defending yourself against any action they take in and out of court.
Further information about our advisory services in connection with the implementation of data protection requirements can be found here.
New legal regulations at European level address supply chain security in particular. The companies concerned are required to ensure that IT security extends to their supply chains as well. Against this backdrop, our team of experts develops effective strategies to protect your company from cyber risks in the supply chain.
There are also new cyber security regulations targeting products with digital elements. To protect users from cyber risks, manufacturers must take cyber security into account as early as the design and development stage for such products. Our specialised team will support you throughout the entire product cycle, from development to obtaining approvals and certificates, to distribution and any obligations after the products reach the end of their life cycle.
In the financial and insurance industries, there have been national, industry-specific regulations on regulatory requirements for IT and IT outsourcing in place for several years, particularly in the form of supervisory notices (Bank Supervisory Requirements for IT (BAIT), Insurance Supervisory Requirements for IT (VAIT), Minimum Requirements for Risk Management (MaRisk), Minimum Requirements under Supervisory Law on the System of Governance of Insurance Undertakings (MaGo), EBA Guidelines on Outsourcing Arrangements, Recommendations on Outsourcing to Cloud Service Providers, etc.). The Digital Operational Resilience Act (DORA) is the first Europe-wide standardised legal framework for effective management of cyber security risks and ICT risks in the financial sector. DORA aims to strengthen the resilience and security of the entire European financial sector and to create standardised and consistent requirements for the financial sector in terms of cyber security, ICT risks and digital operational resilience. Key areas of action include ICT governance, ICT risk management, ICT incident management, digital operational resilience testing and the management of ICT third-party risks. In interdisciplinary teams, we have been advising the financial sector in connection with its digital transformation for many years, including all-round advice on implementing regulatory requirements for IT security and the associated compliance requirements.
Preventive measures are not always successful at stopping cyber incidents. Time and again, attackers manage to penetrate IT systems by exploiting undetected security gaps or human error. Our experts in data protection and IT security law will provide your company with immediate and competent support in the event of a cyber incident, for example helping you to fulfil your statutory reporting obligations and communicating with authorities and stakeholders.
Cyberattacks often result in complex claims relationships between various, often international parties within a supply chain.
A cyberattack can cause immense damage, including the cost of restoring IT systems, reputational damage and lost profits. You may be able to assert claims for damages against other parties involved, such as service providers, manufacturers and many others if they are partly responsible for the cyber incident.
However, there is also the risk of third parties asserting claims against you, for example for breach of contract if you are unable to maintain your business processes as a result of the cyberattack. Customer data may also be affected. There may even be a risk of mass claims – which are becoming more frequent – if data protection rules have been breached.
Our complex disputes experts work with our clients to develop the best litigation strategy to efficiently resolve complex disputes in such situations before the (arbitration) courts or out of court, and achieve the optimal outcome for you, defend you against claims and secure your claims against third parties.
Legal requirements are constantly changing and differ from industry to industry, and this will continue in the future. These requirements include laws, industry-specific safety standards, technical standards, contractual relationships and liability risks. Our future security audit comprises a wide range of advisory services that review the processes and systems currently in place at your company on a regular basis to secure company data from a legal perspective. These regular audits focus on gap analyses, recommendations for the implementation of guidelines, instructions, training and other legal, operational and organisational measures.
Most implementation projects in IT security are highly complex and require the combination of various legal and other external competencies. In our experience, for the legal work involved in such projects to be conducted in an effective and timely manner, it is essential that projects are recorded, planned and managed in line with the company’s objectives and in consultation with stakeholders.
We guarantee this by deploying specialists who have the required expertise and work on the interface between content and organisation, performing the following project-supporting tasks as controllers: (constant) evaluation and definition of the goals and requirements of the transformation, legal project organisation and management of all internal and external resources involved, project planning (definition of work packages, resources, input and output formats), project controlling (transparent open issues, risks, times and expenditures) and project communication (information exchange, jour fixe management and documentation).
We see legal project management as an important discipline that should be provided by legal project managers with specialised legal knowledge rather than a lawyer. This ensures a highly cost-effective approach for each area of expertise.
News
Key Contact >>
![[Translate to English:] Cyber Security Kanzlei A digital microchip is depicted with a glowing padlock symbol on its surface, representing cybersecurity and data protection. The background features abstract lines and nodes, suggesting a networked environment.](/fileadmin/user_upload/AdobeStock_355152474.jpg)










